3.1 XSS Overview
XSS in a nutshell
Cross-Site Scripting (XSS) is a vulnerability that occurs when untrusted data from the user is processed by the web application without validation and is reflected back to the browser without encoding or escaping, resulting in code execution at the browser engine.
Why XSS is dangerous ?
The impact of XSS is moderate for reflected and DOM XSS, and severe for stored XSS, with remote code execution on the victim’s browser, such as stealing credentials, sessions, MFA bypass, DOM node replacement or defacement (such as trojan login panels), key logging or delivering malware to the victim.
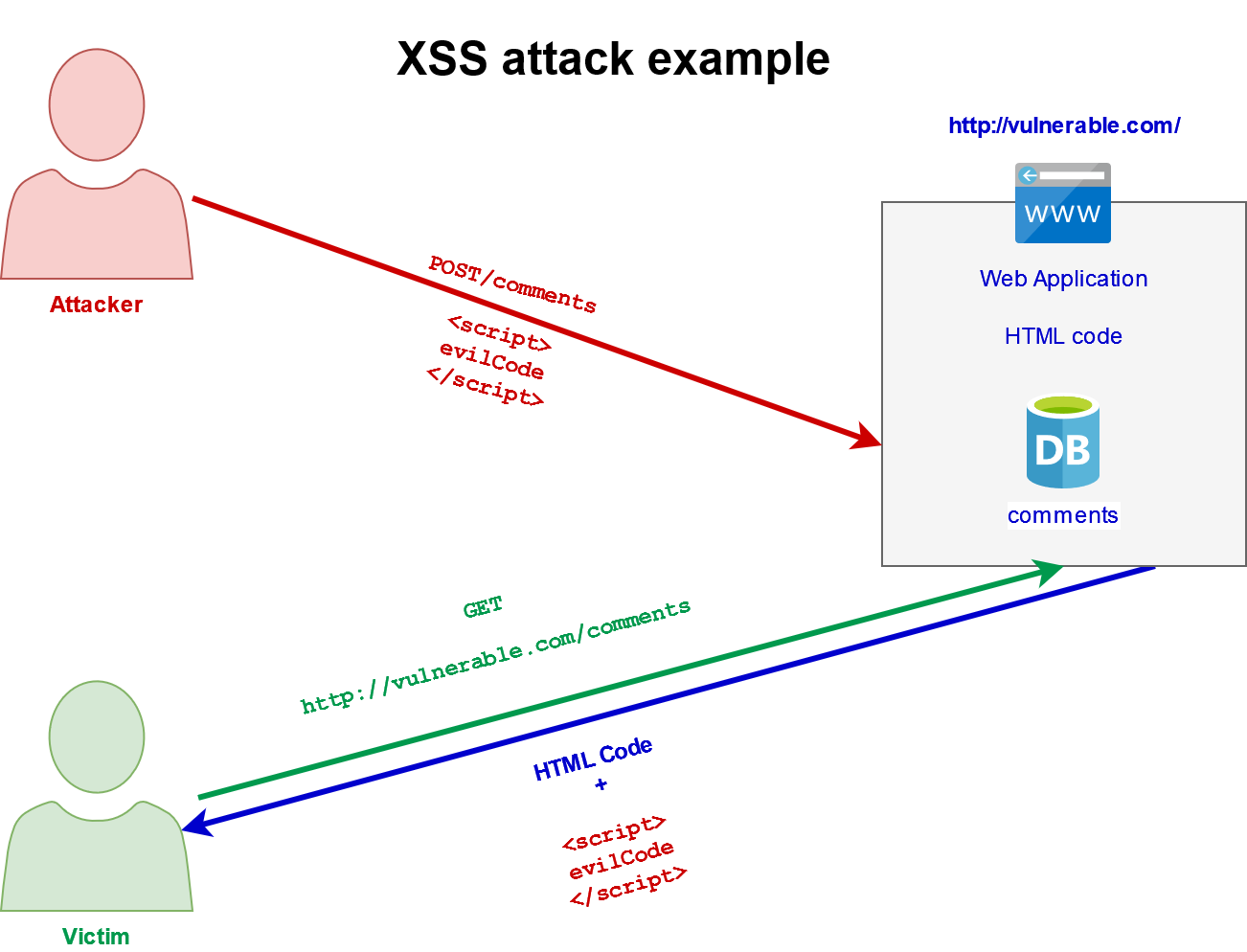
What causes XSS ?
This attack happens mostly because the web application or API uses inputs from any users within the output it generates without proper validation or encoding.
How XSS attacks happen ?
| XSS type | Description | Payload type | Payload Examples | Real cases |
|---|---|---|---|---|
| Reflected | Reflected in web server as an error message, search result or any input sent to the server as part of the request. | From request parameter. |  | epic games |
| Stored | Injected script is permanently stored in target servers. | Stored server-side. |  | myspace worm |
| DOM based | Modifying the DOM environment in the victim browser. | Introduced by DOM modification. |  | Microsoft, Apple, Google,... |
| Mutation | Looks like safe (or just a syntax error) in itself but become active after mutation process | Mutated by browser. |  | Google search bar |
| Blind Cross-Site scripting | Script is saved on server side and reflected back in the backend application. | Tesla |